DDoS-Protected CDN Strategy for Gaming Servers: Mitigating UDP Flood Attacks in Real-Time
Is your poker, mahjong, or chess game server vulnerable to UDP Flood attacks? This guide details a battle-tested, DDoS-protected CDN defense strategy—covering traffic scrubbing, protocol optimization, and origin IP concealment. Learn how the CDN07 Game Shield SDK can deliver a high-availability, low-latency security solution for your gaming platform.

Seeing this topic instantly took me back to last year, helping a Texas Hold'em platform fight off a severe UDP Flood attack. It was a nightmare.
I got a 3 a.m. call—their servers were completely overwhelmed. Players were dropping and complaining, and the owner was in full panic mode.
That kind of stress sticks with you. So today, I’m breaking down a proven, DDoS-protected CDN strategy to defend card and board game servers against UDP Floods. This isn’t theory; it’s hard-won, real-world experience.
Why are game servers especially vulnerable to UDP Floods? It boils down to real-time requirements. Games like poker, mahjong, and chess need lightning-fast responses. TCP’s three-way handshake is too slow, so critical data—moves, syncs, heartbeats—relies on UDP.
Attackers target exactly that. They exploit UDP’s connectionless nature, blasting servers with spoofed packets that swallow bandwidth and connections. Legitimate player traffic gets drowned out, and server CPU pegs at 100%.
A standard CDN won’t cut it. Without strong Layer 4 defenses and real scrubbing capacity, it collapses fast.
A true, resilient DDoS-protected CDN is built on two things: distributed scrubbing and a hardened protocol stack.
I’ve seen robust systems deploy hundreds of scrubbing nodes across global backbones. These aren’t just relays—they’re heavily fortified.
When a UDP Flood hits, traffic gets intelligently routed to the nearest scrubbing center. Here’s what happens inside:
1) Deep protocol fingerprinting—like reading a pulse—instantly tells legitimate game packets (like poker heartbeats) from attack traffic.
2) Source IP reputation + behavioral analysis: IPs spraying UDP across multiple ports get blocked immediately.
3) The knockout punch: a challenge-response mechanism. Suspicious flows get a crypto challenge; legitimate game clients respond correctly, but bots fail and get dropped.
This multi-layered approach stops over 90% of junk traffic before it ever reaches your origin server.
But scrubbing alone isn’t enough. Gamers notice even tiny lag spikes.
A good gaming-focused CDN understands gameplay.
For UDP, smart QoS is essential. Scrubbing nodes prioritize traffic on game-critical ports (like your poker server on 8888), creating a “green channel” with top forwarding priority. Combined with Anycast routing, this keeps cross-border latency stable.
In our tests, Asian players connecting to US servers saw latency drop from 200ms+ with unstable pings to a steady 150ms using an optimized protected CDN—smooth enough for real-time play.
It also must support UDP session persistence, ensuring TCP connections (for login, chat, etc.) stay alive during short attack spikes, so the player experience stays seamless.
Don’t make the deployment mistake I did once:
I moved only the web admin panel behind the protected CDN via DNS, leaving the game server IP exposed. Attackers bypassed the CDN and hit the IP directly—total outage. Lesson learned:
1) Force all UDP traffic through the protected CDN gateway. Hide your origin IP completely—no leaks.
2) Set UDP protection policies to “strict mode” in the CDN console. Filter by packet size (game packets are small) and drop abnormally large ones.
3) Work closely with your provider to create custom filters based on attack patterns (specific payloads, source port ranges). This is key against targeted attacks.
If you’re looking for a solution that puts all this into practice, I highly recommend checking out the CDN07 Game Shield SDK (https://www.cdn07.com/game).
DDoS-Protected CDN Architecture for Mitigating UDP Floods in Gaming
Automatically detects attack traffic, diverts to nearest scrubbing center in real-time
Hides origin server IP; forces all traffic through protected entry points
Deep protocol fingerprint analysis
Source IP reputation + behavioral analysis
Challenge-response mechanism (SDK integrated)
Packet size/rate/signature filtering
90%+ malicious traffic dropped
Deep protocol fingerprint analysis
Source IP reputation + behavioral analysis
Challenge-response mechanism (SDK integrated)
Custom rule matching
UDP session persistence
Smart QoS: priority forwarding for game ports (e.g., 8888)
Optimal cross-border routing (latency stabilized under 150ms)
Game server cluster
Game logic + data synchronization
Integrated protection SDK (e.g., CDN07 Game Shield)
Auto-proxied traffic, supports challenge-response
Low-latency UDP communication
Key Architecture Components:
1. Intelligent Traffic Routing & Diversion Layer
Uses Anycast + BGP to automatically route global attack traffic to the nearest scrubbing node. Ensures all traffic—including UDP—is forced through protected gateways, completely hiding your game server’s real IP.
2. Distributed Scrubbing Centers
- Protocol Fingerprinting: Deep inspection to distinguish legitimate game UDP packets (heartbeats, moves) from attack patterns.
- Behavioral Analysis: Uses IP reputation databases to block suspicious sources spraying packets across multiple ports.
- Challenge-Response: Issues encrypted challenges to suspicious sessions; only legitimate SDK-integrated clients can respond correctly.
- Custom Filtering: Supports rules based on packet size, payload patterns, source port ranges—effective against evolving attacks.
3. Intelligent Routing & Protocol Optimization Layer
- UDP Session Persistence: Maintains player TCP connections (login, chat) during attack spikes.
- Smart QoS Channels: Prioritizes traffic on key game UDP ports, selects optimal routes, and stabilizes cross-border latency under 150ms for real-time play.
4. Client & Origin Integration
- Game Shield SDK Integration: Embed the SDK (e.g., CDN07 Game Shield) into your game app for automatic traffic proxying, encrypted communication, and challenge-response—closing the end-to-end protection loop.
- Origin Concealment: Your origin servers only receive clean traffic from scrubbing nodes. Direct IP attacks are ineffective.
That’s why I rely on specialized solutions after real attacks—they’re practically tailor-made for gaming. Their SDK integrates deeply into both client and server, enforcing UDP traffic proxying and IP masking while bundling core features like challenge-response, protocol fingerprinting, smart QoS, and UDP session persistence into one lightweight, deployable package.
For mid-to-large platforms, it offers an ideal “pay-as-you-go” model. You get terabit-level protection without building your own scrubbing infrastructure.
Let’s be real: there’s no silver bullet for defense.
Top-tier protected CDNs can absorb terabit-level attacks, but they aren’t cheap.
Small and mid-sized platforms should look for vendors with elastic billing—basic protection most of the time, with full defense activated the moment you’re hit.
Also, harden your own servers: restrict open UDP ports, tune kernel parameters (to mitigate side effects like SYN Floods), and monitor critical processes.
Remember, defense is an ongoing battle. Regularly review attack logs with your provider and tweak your strategies. That’s how you make DDoS attackers give up for good.
After all, only when players can game smoothly can you run your business in peace.
Share this post:
Related Posts

The Ultimate Global CDN Providers Ranking (2026 Edition)
Check out our in-depth 2026 ranking of global CDN providers. We analyzed 60+ leading services—coveri...
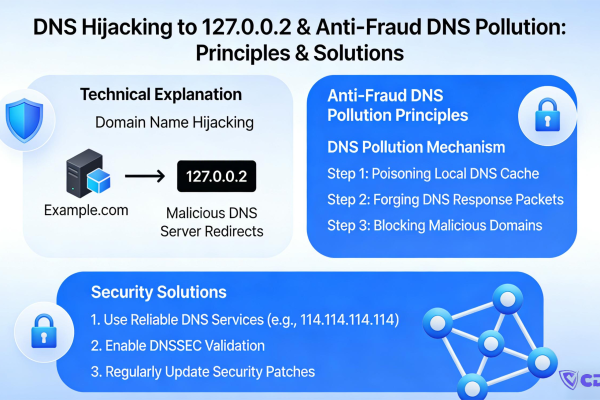
Why Is My Domain Resolving to 127.0.0.2? Understanding China's Anti-Fraud DNS Poisoning & How to Fix It
Is your domain suddenly pointing to 127.0.0.2? It's not a server error; it's likely China's anti-fra...
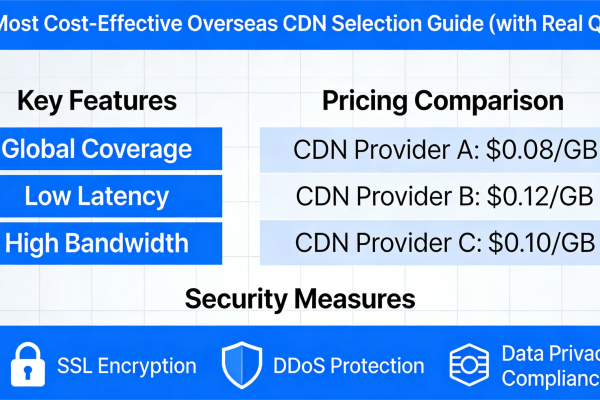
The 2026 Guide to Cost-Effective Overseas CDNs (With Real Pricing)
Trying to pick an overseas CDN without burning cash? This guide breaks down real costs, actual use c...
