No-KYC High-Security CDN Service — The Best Choice for Anonymous Website Protection
Guarding the unnamed, reaching the world. For privacy defenders and sensitive content publishers, we provide high-security CDN services without identity submission (KYC). Through cryptocurrency payments, a strict no-log architecture, and a global Anycast network, we completely isolate your website from your real identity—protecting your anonymity while defending against large-scale DDoS attacks.

Sitting in this Brooklyn café, the cold brew beside me is nearly empty.
Outside, light snow drifts down, but my mind is stuck on a call yesterday from a longtime client. His small independent news site was taken down again by a targeted DDoS attack—the source was obvious.
What chilled him more was that the well-known CDN he was using, under attack pressure, demanded he submit more detailed personal documents for what they called a "secondary KYC verification"—or they’d cut off protection. It felt like being cornered: attackers trying to expose his real identity, and the service claiming to protect him doing exactly the same.
That sense of absurdity is why I’m determined to talk about a high-security CDN that actually lets you breathe anonymously.
The core value of a “No-KYC high-security CDN” lies in those three letters: KYC (Know Your Customer).
Traditional CDN giants, from Cloudflare to Akamai, follow a similar playbook. Want to use our shield? Fine—first tell us who you are, where you live, your company registration number, even a passport scan.
They call it security compliance, anti-money laundering, counter-terrorism financing. That talk might fit the finance world, but forcing it onto every website—especially those publishing sensitive content, operating under pressure, or simply valuing privacy—is a death sentence.
Your identity becomes a ticking time bomb in the provider’s database. If hacked, requested by authorities, or leaked internally, your anonymity goes up in smoke.
Attackers don’t even need to break your server—they can just target the provider, the supposed ally, to find you.
A truly anonymous high-security CDN must solve the problem at its root. First, when registering, you shouldn’t need to provide real name, address, phone, business license—anything that ties back to you.
A temporary email (or encrypted email) to receive a verification link, and a username never linked to your real identity—that’s enough.
The provider shouldn’t want to know—or be able to know—who’s behind the screen. Next, payment is a critical link in the anonymity chain. Mainstream credit cards or PayPal? Those are tied to your real identity.
A reliable anonymous CDN only accepts cryptocurrency, prioritizing privacy coins like Monero (XMR) or mixed Bitcoin. Payments should also be routed through anonymous networks like Tor, cutting off any trail of financial flow.
Finally, the provider’s infrastructure should be built on a “no-log” or “ephemeral log” principle. Your origin server IP, visitor real IPs, request details—either never recorded, or only held briefly in memory for attack analysis. Once an attack stops, the data vanishes. Nothing to hand over, even if asked.
Don’t assume “No-KYC” means weaker protection. Services that survive in this niche do so because they deliver real defense. They typically deploy large global Anycast networks, spreading and diluting attack traffic across scrubbing centers in different regions.
Smart WAF rules and behavior-based DDoS mitigation are standard, able to accurately identify and block malicious requests even in encrypted traffic (including the latest HTTP/3 QUIC)—whether it’s massive SYN/ACK floods, CC attacks, or sophisticated application-layer slow attacks.
Many also include mechanisms like a “challenge wall,” where suspicious traffic must first pass a verification (like a JS challenge) before reaching your origin server—drastically reducing server load. I’ve seen a client’s small blog withstand a mixed attack peaking near 780 Gbps using such a service, while attackers never even glimpsed the real server IP range.
I won’t name specific providers here (you know why), but if you’re looking, keep your eyes open. Check these key points: First, node network coverage and quality—especially connectivity in Asia and Europe. Don’t just trust claims; test routes and latency yourself. Second, transparency in protection capabilities—are they open about scrubbing center capacity and attack types they can mitigate? Vague answers are a red flag.
Third, true payment anonymity—just accepting BTC may not be private enough; support for XMR or ZEC is better. Fourth, do the terms of service clearly state “no-logging” and specify data jurisdiction in privacy-friendly regions (some even place core infrastructure on offshore platforms)?
Finally, check real reputations in tech communities, especially feedback from users who’ve endured sustained high-pressure attacks. That’s more convincing than any flashy ad.
Of course, there’s another side to the coin. Choosing this kind of service means giving up some conveniences of “mainstream” providers—like 24/7 phone support for complex setups (anonymous services usually only offer ticketing or encrypted chat).
The providers themselves may be more fragile, with higher operational risks. Most importantly, it’s a legal gray zone: you’re responsible for your content. Anonymity isn’t a shield for illegal activity. If you host clearly illegal material (like child exploitation or terrorism), the provider will likely terminate your service—and their infrastructure could attract law enforcement attention.
This tool is, at its heart, a megaphone for those speaking truth—not a pathway for crime.
The snow has stopped. The café heater hums softly. Watching people hurry past outside, each with their own story to hide and their own voice to share.
In the digital world, anonymity isn’t a sin—it’s a fragile barrier protecting a fundamental right. When what you say could bring danger, a truly no-KYC, no-financial-trail, technically robust high-security CDN is the closest thing to a “safe house” you’ll find in cyberspace.
It doesn’t guarantee absolute safety, but it gives you a fighting chance—letting your voice be heard, rather than silenced the moment your identity is exposed.
Remember, true protection begins when your opponent doesn’t know where you are.
(Words: KRA)
Share this post:
Related Posts

The Ultimate Global CDN Providers Ranking (2026 Edition)
Check out our in-depth 2026 ranking of global CDN providers. We analyzed 60+ leading services—coveri...
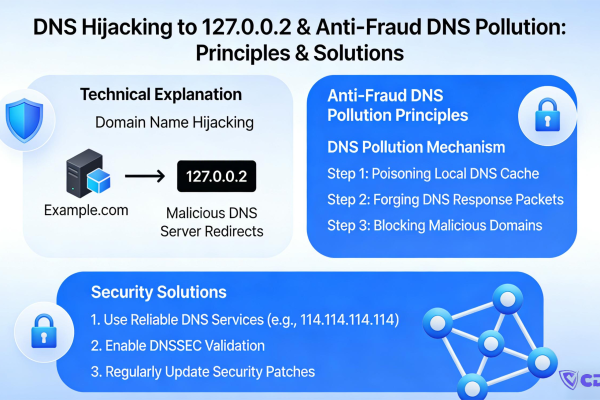
Why Is My Domain Resolving to 127.0.0.2? Understanding China's Anti-Fraud DNS Poisoning & How to Fix It
Is your domain suddenly pointing to 127.0.0.2? It's not a server error; it's likely China's anti-fra...
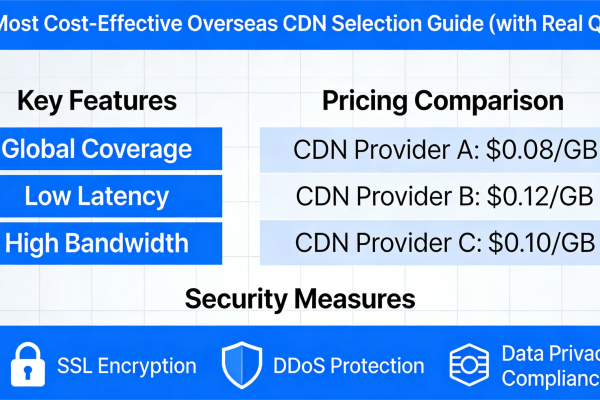
The 2026 Guide to Cost-Effective Overseas CDNs (With Real Pricing)
Trying to pick an overseas CDN without burning cash? This guide breaks down real costs, actual use c...
