The Most Comprehensive DDoS Protection Solution Comparison: DDoS Protected IP, Anycast, or BGP Scrubbing – Which to Choose?
A full comparison of DDoS protection solutions: DDoS Protected IP, Anycast, and BGP Scrubbing. We explain how they work, their pros and cons, and ideal use cases to help your business find the most stable and suitable defense system.
When a business gets hit by a DDoS attack for the first time, the reaction usually boils down to two things:
First, panic. Second, a sense of unfairness.
"I'm just running a regular website, a cross-border store, or an API service – why would anyone attack me?" But the reality is this:
If you're on the internet, you will be attacked. It's only a matter of time.
In this article, I'll break down the truly crucial parts in plain language:
- What exactly is a DDoS attack? Why are they getting more severe?
- What are the common protection solutions, and which fit which type of business?
- How do you actually choose between a DDoS Protected IP, Anycast, and BGP Scrubbing?
- How can you tell if a protection service is genuinely strong or just "slide-deck security"?
If DDoS attacks have left you anxious and confused, this article will clear things up.
1. What's Up with DDoS? Why Is It Getting Harder to Stop?
The essence of a DDoS (Distributed Denial of Service) attack is simple:
To overwhelm your server until it becomes unusable.
But defending against it is tough for two main reasons:
1. The Cost of Attack is Too Low
In the past, launching a DDoS required skill and resources. Not anymore.
You can spend a few bucks on the dark web to rent a "stresser" platform,
and take a website down with a couple of clicks.
Attacks cost pennies; defense costs thousands, even tens of thousands.
It's an asymmetric game from the start.
2. Modern Business Relies Heavily on Real-Time Network Response
Typical examples:
- Cross-border e-commerce: Users bounce if they can't click through.
- API services: High latency basically means the service is down.
- Login/Checkout systems: A single hit can mean lost orders.
- Finance/Trading: A 5-second delay can cause an incident.
Attackers are smart too; they target your peak traffic hours and promotional events.
So you'll find:
Ten years ago, DDoS was a big-company worry. Now, it's an everyday risk for any website.
 2. What Are the Main DDoS Protection Solutions?
2. What Are the Main DDoS Protection Solutions?
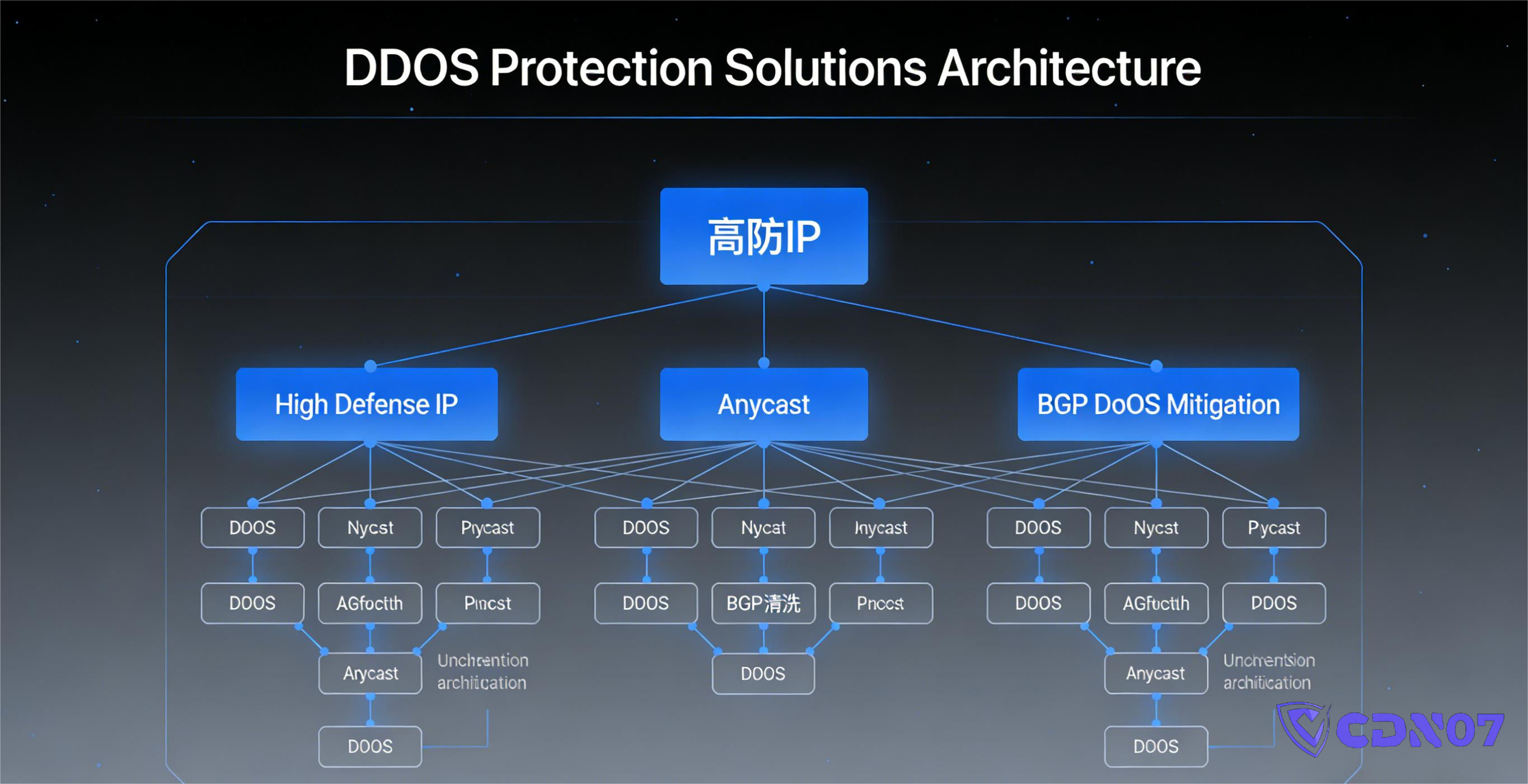
The technical approaches on the market mainly fall into three categories:
- DDoS Protected IP (Fixed Entry Point + Scrubbing Center)
- Anycast Distributed Protection (Multiple Entry Points + Global Traffic Routing)
- BGP Scrubbing Nodes (Carrier-Grade Protection)
Some CDN providers also mix and match these three approaches.
Below, I'll explain their differences in the simplest terms.
3. Option 1: DDoS Protected IP – The Most Traditional & Common Method
The idea behind a DDoS Protected IP is straightforward:
All attack traffic is sent to this single protected IP. A "scrubbing center" in a fortified data center filters out the junk traffic and forwards only clean traffic to your server.
Think of it as:
Adding a "crash barrier and drainage ditch" to your website.
Advantages of a DDoS Protected IP:
1. Relatively Predictable Cost
Basic protection for a few tens of Gbps won't break the bank.
2. Good for Fixed Entry Points
For example:
- Website homepage
- Game login server
- API endpoint
If the entry point is fixed, it's easy to integrate with this protection.
3. Simple Management
Usually just requires a DNS change or setting up a reverse proxy with the provider.
Disadvantages of a DDoS Protected IP:
1. Single Point of Failure Risk
There's only one entry point. If attackers concentrate their fire on this single spot, the pressure is immense.
2. The Scrubbing Center Might Be Far Away
For example, if users are in Asia but the scrubbing center is in Europe or the US, it adds extra latency.
3. Can Struggle with Tbps-Level Attacks
If the attack volume exceeds your plan's capacity, your IP gets null-routed (blackholed) or throttled.
Best Use Cases for a DDoS Protected IP:
✔ Game login servers ✔ Services with fixed IPs (APIs, admin panels) ✔ Businesses with traffic primarily from one region ✔ Small/medium websites, independent stores, corporate sites
In a nutshell:
If you're on a budget but need a stable entry point, a DDoS Protected IP is a solid first choice.
 4. Option 2: Anycast Protection – Currently the Strongest Anti-DDoS Architecture
4. Option 2: Anycast Protection – Currently the Strongest Anti-DDoS Architecture
If you ask:
"What's the best defense against large-scale attacks today?"
The answer is definitely: Anycast Distributed Protection.
Its logic is completely different from a simple Protected IP:
The core of Anycast is "multiple entry points," not a single fixed one.
A simple analogy:
If a Protected IP is one big gate, then Anycast is:
Dozens of gates open simultaneously around the world. Users enter through the nearest one, and attacker traffic is spread across different regions, preventing a single point from being overwhelmed.
This is called:
"Distributed Attack Dilution"
An attacker sends 500 Gbps, but in an Anycast network, it might be distributed as:
- 40 Gbps to Japan
- 60 Gbps to Korea
- 80 Gbps to Hong Kong
- 100 Gbps to Singapore
- 120 Gbps to Europe
- 100 Gbps to the US
No single point gets overwhelmed.
Advantages of Anycast:
1. Extremely High Defense Capacity (Can handle Tbps-level)
Because attacks are digested across multiple points.
2. Faster Access for Users
Traffic routes to the nearest node, reducing latency.
3. Smarter Scrubbing, More Flexible Traffic Management
During an attack:
- Node under heavy load? → Traffic automatically rerouted.
- Network path congested? → Automatically finds an alternate route.
- One region under attack? → Other regions provide backup.
This is something ordinary Protected IPs can't do.
Disadvantages of Anycast:
1. High Cost
Multiple distributed nodes, expensive data centers, costly bandwidth, and high technical barriers.
2. Complex Setup, Stricter Configuration
Especially for origin traffic routing, port configuration, and security policies.
3. Not Ideal for Services Requiring a Fixed Origin IP
For example, some payment gateways require a fixed, whitelisted IP address.
Best Use Cases for Anycast:
✔ Global user base ✔ Huge attack scale (100–800 Gbps+) ✔ Gaming, finance, trading platforms ✔ SaaS products, API platforms ✔ Independent stores / Cross-border e-commerce
Bottom line:
For stability, speed, and the ability to withstand massive attacks, Anycast is the gold standard.
 5. Option 3: BGP Scrubbing – The Common "Carrier-Grade" Protection in China
5. Option 3: BGP Scrubbing – The Common "Carrier-Grade" Protection in China
BGP Scrubbing is typically used for attack scenarios within China.
Its principle is:
The carrier (ISP) performs scrubbing on its own backbone network, filtering attacks closer to the source.
Think of it this way:
The attack traffic gets intercepted on the carrier's highway before it even reaches your data center.
Advantages of BGP Scrubbing:
1. High Performance, Low Latency
Low latency across China's three major networks (China Telecom, China Mobile, China Unicom), ideal for a domestic audience.
2. Strong Scrubbing Capacity (Hundreds of Gbps to Tbps)
ISP backbone bandwidth is inherently massive.
3. Wide Coverage
Major Chinese carriers generally offer BGP protection solutions.
Disadvantages:
1. High Cost (especially for true, high-quality BGP)
Real BGP nodes are very expensive, not something every data center can afford.
2. Poor Fit for Cross-Border Business
BGP is optimized for domestic traffic, not ideal for international websites.
3. Traffic Management Less Sophisticated Than Anycast
BGP focuses on "domestic stability," not a global distribution model.
Best Use Cases:
✔ Websites with a primarily Chinese user base ✔ Game servers in China ✔ Government and enterprise services ✔ Internal systems with high-security requirements
To summarize:
Mainly domestic traffic → BGP Scrubbing is more suitable.
Cross-border traffic → Anycast or CN2-based solutions.
Single entry point → DDoS Protected IP.
6. Side-by-Side Comparison Table (See the Key Differences at a Glance)
| Solution | Defense Capability | Best For | Cost | Access Speed | Capacity vs. Large Attacks | Key Strength |
|---|---|---|---|---|---|---|
| DDoS Protected IP | ⭐⭐⭐⭐ | Single entry point services, APIs | Medium | Medium (depends on data center) | Medium | Cost-effective, simple to set up |
| Anycast | ⭐⭐⭐⭐⭐ | Global services, Cross-border services | High | Fastest (nearest node) | Extremely Strong (Tbps-level) | Distributed attack dilution, smart routing |
| BGP Scrubbing | ⭐⭐⭐⭐ | Domestic (China) services | High | Fast within China | Strong | Carrier-grade scrubbing, domestic stability |
7. So, Which One Should Your Business Choose?
Here's the most practical way to decide:
If your main users are in Mainland China:
✔ BGP Scrubbing ✔ Domestic DDoS Protected IP
If you run cross-border e-commerce, overseas projects, or a global SaaS:
✔ Anycast Protection (priority) ✔ Hybrid solutions with CN2/multi-path origin routing ✔ Protected CDN with overseas nodes
If you're on a tight budget:
✔ Start with a DDoS Protected IP ✔ Upgrade to Anycast if attacks grow larger
If your business falls into these categories, consider Anycast from the start:
- Gaming
- Finance / Trading
- Frequent logins/registrations
- API / Interface services
- Backend systems highly sensitive to stability
- Mostly dynamic websites
Attackers love targeting these services. Anycast provides peace of mind.
8. How to Tell If a Protection Service Is Actually Strong?
A defense system isn't defined by just "100G" or "1000G" claims. Ask these 5 questions:
1. How many scrubbing centers do they have? Where are they located?
A provider with only one scrubbing center will struggle with large-scale attacks.
2. Do they support geo-distributed scrubbing?
Can they intelligently reroute traffic during an attack? Does traffic automatically shift if a node reaches capacity?
3. Is origin routing intelligent? Does it support multi-path origin routing?
Relying on a single, fixed path back to your origin server is an easy weak point for attackers to exploit.
4. What's their AI/behavioral analysis capability like?
Key capabilities include:
- Browser fingerprinting
- Human/bot behavior modeling
- Automatic blocking of anomalous access
- Intelligent HTTP Flood identification
If they rely solely on IP blacklists, their methods are outdated.
5. Do they provide real-time attack analytics and logs?
Many so-called "high-defense" services only show static numbers, hiding the real attack data. A truly capable provider offers near real-time logs (e.g., 5-second granularity).
9. The Essence of DDoS Protection: It's Not About "Absorbing" Hits, But "Staying Online"
Many businesses misunderstand DDoS protection, thinking the goal is "how much can it absorb."
But the real question is:
Can your business remain stable during an attack?
As long as your website loads, your APIs respond, and your admin panel is accessible, it doesn't matter how long the attack lasts.
So the ultimate goal isn't "absorbing," but achieving:
Stability + Speed + No Blackholing + A Seamless User Experience.
10. There's No One-Size-Fits-All Solution, Only the Right Architecture for You
Here's the most practical summary:
- Tight budget? A DDoS Protected IP is enough to start.
- Domestic (China) business? BGP Scrubbing is best.
- Cross-border + globally dispersed users? Anycast is a must.
- High-frequency, dynamic business? Use Anycast sooner rather than later.
- Facing massive attacks? Distributed protection (Anycast) is the endgame.
Protection isn't a one-time purchase; it's an ongoing process.
But with the right solution in place, your website can stay as stable as if nothing happened.
Share this post:
Related Posts
No-ICP CDN Recommendations | Which Ones Actually Speed Up Mainland China AND Can Withstand Attacks?
How to choose a no-ICP CDN? Based on real webmaster tests, this article compares multiple CDN provid...
What's the Difference Between DDoS-Protected CDN and DDoS-Protected IP? A Clear Guide to Help You Choose.
What's the difference between a DDoS-protected CDN and a DDoS-protected IP? Which one should your we...
Which CDNs Support No-KYC Signup? And Which Providers Also Accept USDT Payments?
Which CDNs allow no-KYC signup and support USDT payments? We tested providers like CDN07 and Gcore—c...
