Can You Trust Those "Top DDoS-Protected CDN" Lists? The Truth Revealed by a Veteran Webmaster
Are "Top DDoS-Protected CDN" lists actually reliable? Drawing from years of hands-on testing, this guide breaks down the pros and cons of security-focused CDNs—from defense mechanisms and scrubbing to node architecture and true cost—helping you cut through the marketing hype and choose the right protection for your site.
If you've ever searched for "DDoS-protected CDN recommendations" online, you've probably come across lists like these:
"Top 10 DDoS-Protected CDNs for 2026"
"Global Ranking of the Most Powerful DDoS Defense CDNs"
"Vendor X Boasts 10 Tbps Protection Capacity"
They look professional, with specs that seem more impressive each time. But the real experience for many webmasters after signing up is this:
Attacks still get through, site speed is still sluggish, and the bills just keep getting bigger.
With over a decade in cybersecurity and site protection, I've tripped into my fair share of pitfalls and have personally tested numerous DDoS-protected CDN solutions. I can tell you this with confidence:
Most "Top DDoS-Protected CDN" lists have limited practical value and can often lead you to make poor decisions.
In this article, I'm not pushing any service or taking sides. I'm just sharing the facts you genuinely need to know.
1. Why Are Most Online "Top DDoS-Protected CDN" Lists Untrustworthy?
Let's cut to the chase: The problem isn't the list itself, but its "evaluation logic."
1️⃣ Lists Compare "Specs," Not "Whether It Actually Holds Up"
You'll see loads of information like this in those rankings:
- Protection Capacity: 500 Gbps / 1 Tbps / 10 Tbps
- Number of Nodes: 200+ / 300+
- Countries Covered: 100+
But in reality, what takes your site down is never "insufficient specs," but rather:
- Whether the attack is accurately identified
- How fast the scrubbing happens
- Whether your origin server gets overwhelmed
- If legitimate traffic can still get through during an attack
Specs are just marketing. User experience is the only result that matters.
2️⃣ Many Lists Are Essentially "Paid Recommendations"
I don't need to spell this out too clearly—you get the idea.
- Higher-paying vendors get top spots
- Vendors partnered with the listing platform get "featured"
- Those who don't play ball disappear from the list entirely
Truly impartial, technically-driven rankings are exceedingly rare.
3️⃣ Lists Don't Tell You the "Prerequisites for Use"
Many high-protection CDNs look impressive on paper, but they often assume one critical condition:
That your website architecture, traffic patterns, and business type happen to be a perfect fit for their system.
The reality is different:
- Dynamic and static sites require completely different protection strategies.
- API-based services and content-heavy sites need different scrubbing logic.
- A site serving mainly domestic traffic vs. international traffic demands different node strategies.
A list won't help you figure this out.
2. What Problems Does a DDoS-Protected CDN Actually Solve?
Before we go further, let's clarify the core concept.
A DDoS-protected CDN is not primarily a "make-my-site-faster" tool. Its number one job is this:
To keep your website accessible during an attack.
It tackles three main issues:
- DDoS Attacks (volumetric, connection-based)
- CC Attacks (mimicking legitimate users to exhaust resources)
- Malicious Scanning / Abnormal Requests (slowly draining your resources)
Speed is a bonus. Staying protected is the core mission.
3. In Real-World Tests, What Makes a DDoS-Protected CDN Effective?
Many webmasters assume:
"High protection rating = Large bandwidth = It can handle attacks"
This is a very common misunderstanding.
1️⃣ The Real Core is Scrubbing Capability, Not Bandwidth
The basic working principle of a protected CDN is simple:
- Legitimate Traffic → Allow
- Malicious Traffic → Identify → Discard
The key isn't "how much water can come in," but rather:
- Can it tell the dirty water from the clean?
This involves:
- Behavioral Analysis
- Request Frequency
- Protocol Fingerprinting
- Request Fingerprinting
- AI-Powered Judgement Models
This is the part lists almost never detail.
2️⃣ Node Architecture is Far More Important Than Node Count
Many lists boast "200+ global nodes," but what I care about is:
- Are the scrubbing nodes independently deployed?
- Will attack traffic take down the standard acceleration nodes first?
- Is scrubbing separated from origin pull traffic?
In reality, many "budget" protected CDNs mix scrubbing and acceleration. When a major attack hits, site access plummets.
3️⃣ AI Scrubbing Isn't a Gimmick, But It's Not a Magic Bullet Either
Nearly every vendor now talks about "AI Protection" and "Intelligent Scrubbing."
To be honest, it's not false, but it's often exaggerated.
The real situation:
- AI is better at handling sustained, patterned attacks.
- For short, massive flood attacks, robust infrastructure is still critical.
- False positives and blocking legitimate traffic still happen, though less frequently.
AI is a value-add, not a lifesaver.
4. 5 Critical Points Most "Top CDN" Lists Overlook
If you only look at lists, you'll likely miss these factors that truly impact your experience.
1️⃣ Attack Activation Threshold
Some so-called protected CDNs:
- Advertise 500 Gbps protection
- But start throttling or dropping legitimate traffic during a 10 Gbps attack
Lists won't tell you these details.
2️⃣ Scrubbing Latency
When an attack hits:
- Does it switch to scrubbing in under 3 seconds?
- Or does it take 30 seconds?
- Is manual intervention required?
This determines if your site has a "minor hiccup" or goes "completely offline."
3️⃣ Is Origin Protection Actually in Place?
Many sites go down not because the frontend is overwhelmed, but because:
- The origin server IP is exposed
- The origin pull path gets saturated
- Protection is only at the CDN layer, leaving the origin server vulnerable
Lists rarely mention this.
4️⃣ Service Quality During an Attack
Stopping an attack is one thing. Remaining usable while under attack is another.
- Does page load time increase significantly?
- Do APIs start timing out?
- Do logins or payment processes fail?
You only know this from real-world use.
5️⃣ The Cost Curve, Not Just the "Starting Price"
Many protected CDNs:
- Have an attractive entry-level price
- But costs skyrocket once your traffic or attack frequency increases
Lists say "reasonably priced" but don't tell you how expensive it gets over time.
5. How Should You Actually Choose a DDoS-Protected CDN? A Method More Reliable Than Lists
If you want my most practical piece of advice:
Don't ask "which one is the best." Ask "which one is the best fit for my *current* business situation."
Start by answering these questions:
✔ What's my business type?
- Static content site?
- Dynamic application?
- API / backend service?
✔ How frequent are the attacks?
- Occasional probes?
- Regular targeting?
- Constant, persistent attacks?
✔ Where are my users primarily located?
- Mainland China
- Overseas
- A mix
✔ What's my actual budget ceiling?
- The cost of one successful breach
- The monthly cost for sustainable, long-term protection
These questions are more important than any list.
6. A Final Word of Truth for Fellow Webmasters
Here's some blunt honesty:
"Top DDoS-Protected CDN" lists are useful for initial research, not for copy-pasting your buying decision.
A truly reliable protection plan usually comes from:
- Tailoring the solution to your specific business
- Testing and comparing multiple options
- Evaluating real-world performance, not marketing pages
If your site is already under attack or your business has steady revenue, trust lists even less.
With security, going cheap once can cost you many times over.
FAQ:
Q1: What's the biggest difference between a standard CDN and a DDoS-protected CDN?
A: Standard CDNs focus on acceleration. DDoS-protected CDNs have attack identification and traffic scrubbing as their core function; acceleration is secondary.
Q2: Is a DDoS-protected CDN always better than a DDoS-protected IP?
A: Not necessarily. Protected CDNs are ideal for public-facing websites. Protected IPs are often better for backend services, APIs, or non-public infrastructure.
Q3: Are higher defense specs always better?
A: Specs show potential capacity. What matters more are the scrubbing policies and activation mechanisms.
Q4: Are free or very cheap DDoS-protected CDNs reliable?
A: They might work for testing, but are risky for long-term or critical business use. Real attacks quickly expose their weaknesses.
Q5: After being attacked once, do I need a protected CDN long-term?
A: If attacks are persistent or targeted, long-term protection is usually more cost-effective than repeated emergency fixes.
Share this post:
Related Posts
Hong Kong High-Defense CDN Recommendations (2026 Latest Edition)
Not all Hong Kong high-defense CDNs can withstand attacks. This article compares the protection stre...
No-ICP CDN Recommendations | Which Ones Actually Speed Up Mainland China AND Can Withstand Attacks?
How to choose a no-ICP CDN? Based on real webmaster tests, this article compares multiple CDN provid...
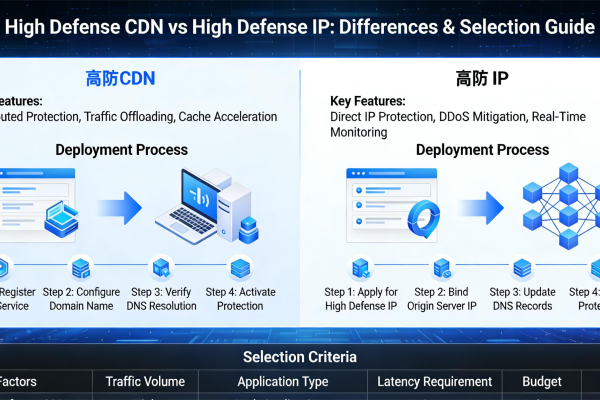
What's the Difference Between DDoS-Protected CDN and DDoS-Protected IP? A Clear Guide to Help You Choose.
What's the difference between a DDoS-protected CDN and a DDoS-protected IP? Which one should your we...
