DoS vs DDoS: What's the Difference & What is a DDoS Protected IP?
A straightforward explanation of DoS vs DDoS, plus a deep dive into DDoS Protected IP: how it works, its benefits, ideal use cases, and common myths. A must-read for webmasters looking to implement proper defense.
Here's a hard truth you'll learn if you run a website long enough: What takes a site down isn't poor server specs—it's DDoS.
Most people have heard of DoS, DDoS, and "High Defense IPs" but don't really understand them. In this article, I'll break it all down in plain English, drawing from over a decade of experience in security, protection, and CDN work.
Contents
- Introduction: Why You Should Read This
- 1. The One-Sentence Difference Between DoS and DDoS
- 2. Why No One Really Uses DoS Anymore
- 3. What Makes DDoS So Dangerous
- 4. What is a DDoS Protected IP?
- 5. How a Protected IP Shields Your Website
- 6. Why "Cheap Server + Free CDN" Fails Against DDoS
- 7. When You Absolutely Need a Protected IP
- 8. How to Choose a Reliable DDoS Protected IP Provider
- 9. Common Mistakes Webmasters Make
- 10. Practical Advice: A More Robust Defense Strategy
- FAQ
1. The One-Sentence Difference Between DoS and DDoS
The short version:
DoS (Denial-of-Service): One person throwing a punch.
DDoS (Distributed Denial-of-Service): A crowd attacking you all at once.
To put it even more simply: DoS uses one machine to flood a target with requests. DDoS uses thousands of hijacked "botnet" machines to do the same thing, simultaneously.
DDoS is far more destructive than DoS, yet ironically cheaper to launch—which is why it's the dominant threat today.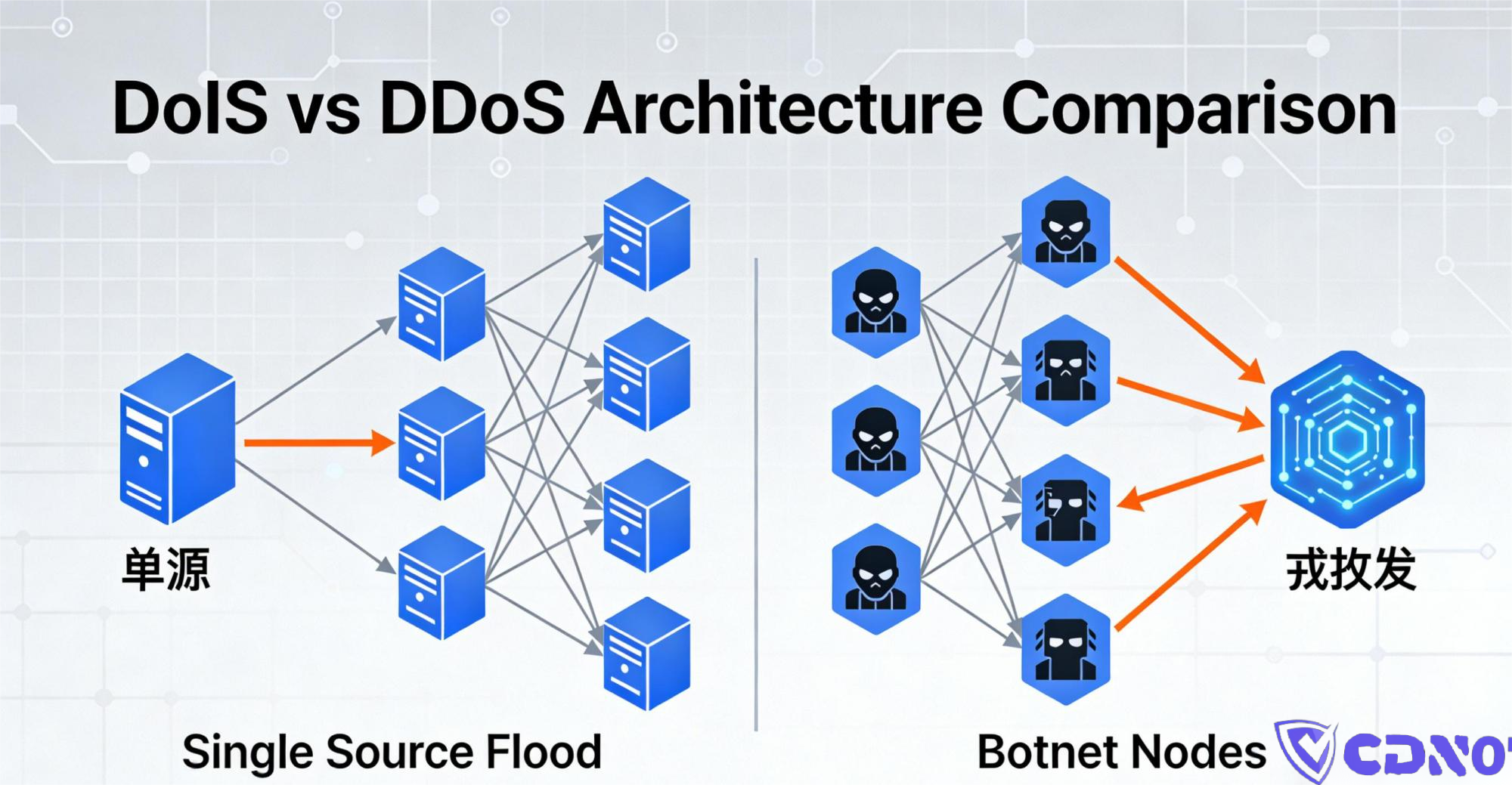
2. Why No One Really Uses DoS Anymore
DoS is largely obsolete. Here's why:
- A single machine has limited bandwidth, making attacks less effective.
- Modern servers are much more powerful.
- Networks often have filters to block such simple traffic floods.
- DDoS attacks are cheap and accessible to anyone with basic skills.
Today, almost all attacks are DDoS-based. They're cost-effective, powerful, and difficult to defend against.
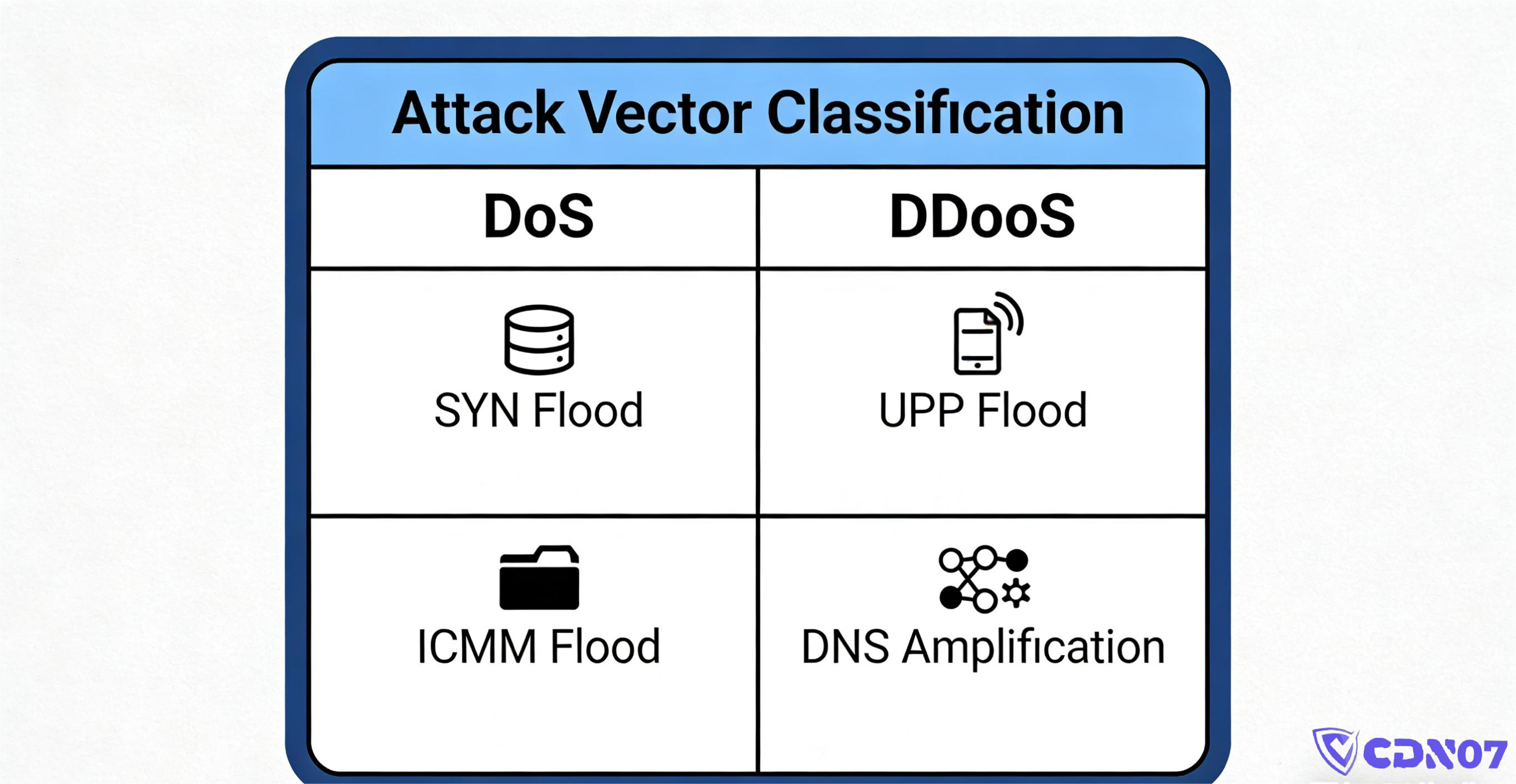
3. What Makes DDoS So Dangerous
Why does the mere mention of DDoS make site owners nervous? Because it can make your online business vanish in an instant.
Its destructive power comes from:
- Massive Bandwidth Scale: Attacks commonly reach tens or even hundreds of Gbps.
- Multiple Attack Vectors: UDP Flood, TCP SYN Flood, HTTP Flood, CC Attacks... it's a barrage of different methods.
- Strong Camouflage: Malicious traffic blends in with legitimate user visits, making it hard to filter.
- Long Duration: Attacks can last for hours, days, months, or even longer.
A standard server simply can't withstand this.
4. What is a DDoS Protected IP?
A DDoS Protected IP is essentially this: A security provider gives you a specially fortified IP address. All traffic—including attacks—is sent to this IP first. The provider filters out the malicious traffic and forwards only the clean, legitimate traffic to your actual server.
Think of it as a combination of:
Bulletproof Shield + Buffer Zone + Scrubbing Center
You simply point your domain name or service to this Protected IP, and your origin server never directly faces the attack.
For more details, check out What is a DDoS Protected IP? A Complete Guide from Attack Types to Defense Principles.
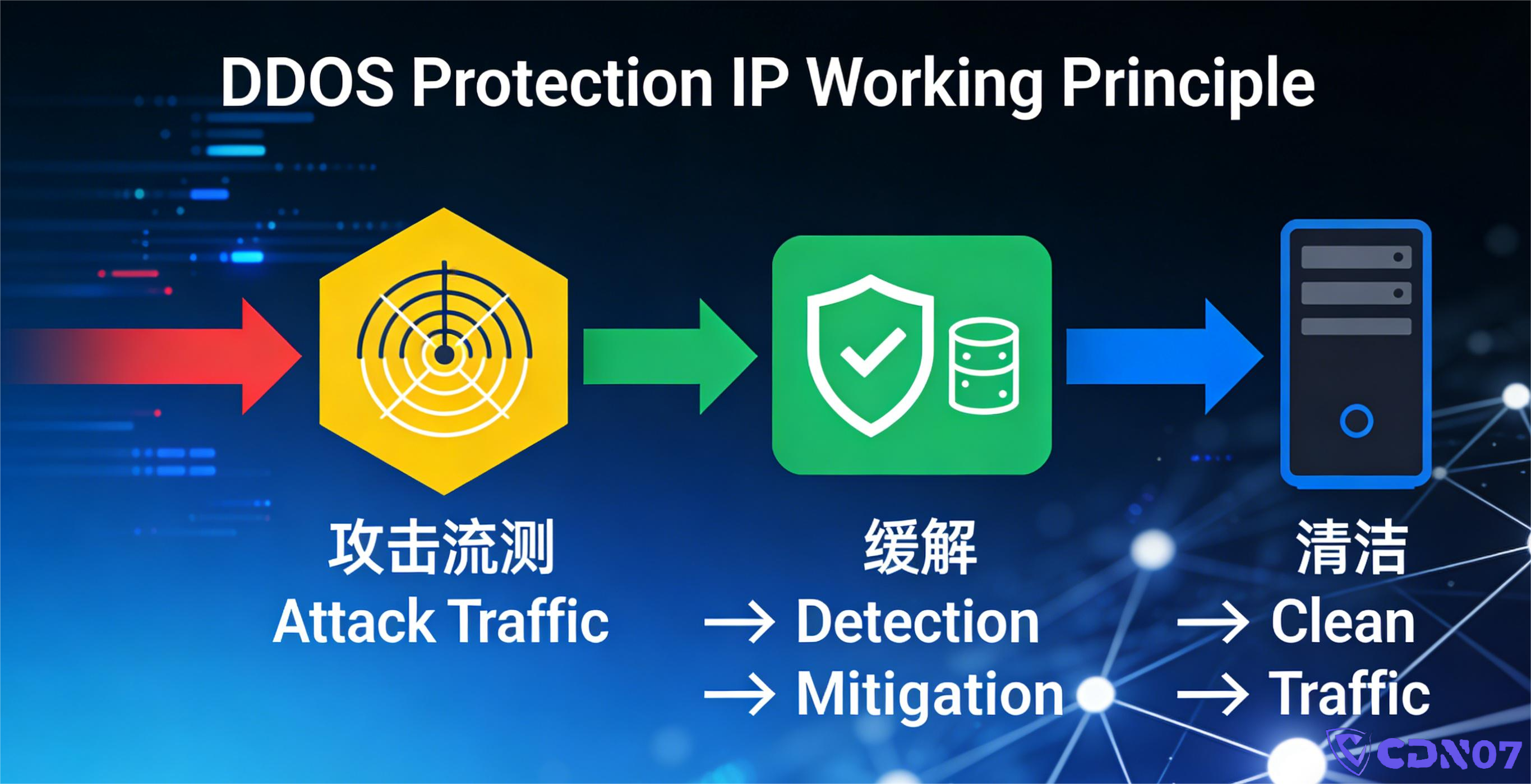
5. How a Protected IP Shields Your Website
A robust DDoS Protected IP service typically handles attacks in several key ways:
① Absorbs the Attack at the Edge
The provider's data centers have massive bandwidth (hundreds of Gbps to multiple Tbps) to ingest the initial attack traffic.
② Filters Traffic Through "Scrubbing" Systems
These advanced systems can identify and block:
- Fake requests
- Repetitive requests
- Traffic with abnormal request rates
- Bots with spoofed IPs or User-Agents
③ Distinguishes "Users" from "Attackers" Based on Behavior
This is the core capability:
- Human Visitors: Allowed through normally.
- Crawlers/Bots: Rate-limited.
- Attack Traffic: Dropped completely.
④ Forwards Only "Clean Traffic" to Your Origin
Only legitimate requests that are meant for your website reach your origin server, drastically reducing its load.
6. Why "Cheap Server + Free CDN" Fails Against DDoS
Many webmasters think a free CDN like Cloudflare's basic plan can stop major attacks. The reality is different.
Free CDN = Basic Protection + Shared Resources. It is NOT DDoS protection.
Reasons why free CDNs can't handle real DDoS attacks:
- Limited node bandwidth.
- Shared IPs—if another user on the same IP gets hit, your site suffers too.
- Advanced security rules are locked behind paywalls.
- Ineffective against high-volume HTTP Flood/CC attacks.
- For users in regions like China, traffic may be routed inefficiently, causing high latency.
The purpose of a free CDN is "acceleration + basic security," not "attack mitigation."
7. When You Absolutely Need a Protected IP
You should strongly consider a DDoS Protected IP if:
- You've been attacked before (especially if you're being targeted).
- You run an international business prone to malicious attacks.
- You're in a high-risk or competitive industry (live streaming, e-commerce, gaming, news/media).
- Your site has admin panels, login interfaces, or payment gateways.
- Your website is frequently scanned or probed.
In these scenarios, the cost of downtime from an attack far outweighs the cost of protection.
8. How to Choose a Reliable DDoS Protected IP Provider
Evaluate providers based on these criteria:
① Bandwidth & Scale
Look for a defense capacity of at least 500Gbps to 2Tbps.
② Support for Multi-Vector Scrubbing
The service should defend against:
- UDP Flood
- TCP SYN Flood
- HTTP Flood / CC Attacks
- Slow Connection Attacks (e.g., Slowloris)
- Advanced Bot Behavior Identification
③ Uptime & Stability (Critical)
Protection isn't about surviving one attack, but providing consistent, stable defense.
④ Origin Network Quality
If the return path (from the protected IP to your server) is poor, your site will still be slow for legitimate users.
⑤ Support for Auto-Blocklists & Behavioral Learning
Smarter systems adapt to new threats and save bandwidth and costs in the long run.
9. Common Mistakes Webmasters Make
Mistake 1: Thinking a CDN equals full protection.
A CDN is not a DDoS mitigation service, especially the free tier.
Mistake 2: Believing changing your server IP will solve the problem.
Attackers can scan and find your new IP address within minutes.
Mistake 3: Assuming a more expensive server can withstand attacks.
No matter how powerful your server is, its bandwidth is no match for a large-scale DDoS.
Mistake 4: Trying to write your own firewall rules.
Too many rules block real users; too few let attacks through. It's an endless, losing battle.
10. Practical Advice: A More Robust Defense Strategy
If your business has already suffered attacks, here's a solid setup:
- Place a Protected CDN / DDoS Protected IP in front.
- Host your origin server in a region with excellent network quality (e.g., Hong Kong, Japan, Singapore).
- Enable a Web Application Firewall (WAF), anti-probing measures, and rate limiting.
- Apply extra protection to admin/backend interfaces.
This offers the best balance of cost-effectiveness, stability, and low maintenance.
FAQ (Frequently Asked Questions)
1. What's the difference between a DDoS Protected IP and a "High Defense Server"?
A Protected IP is a defense layer you put in front of your existing server. A "High Defense Server" typically bundles the protection with the physical/virtual server hardware. The IP solution is more flexible; the bundled server is often more costly.
2. Will a Protected IP slow down my website?
No. It usually improves stability because attacks are filtered before they reach your origin server, preventing overload.
3. Is Cloudflare considered a DDoS protection service?
The free plan is not. Their paid Enterprise plans, however, offer robust, large-scale DDoS mitigation.
4. Can a DDoS Protected IP itself be taken down?
In theory, anything can be overwhelmed. However, reputable providers have dynamic bandwidth scaling and massive network capacity, making it extremely difficult to "take down" their protection layer.
5. Can I just use a WAF and skip DDoS protection?
No. A WAF protects against application-layer (HTTP/HTTPS) attacks. DDoS attacks often target the network/transport layer (like UDP/TCP floods), which a WAF cannot stop.
Final Word:
If your website has value, you must factor DDoS risk into your planning.
The cost of launching attacks is dropping, while the cost of downtime is soaring.
Being prepared is always better than trying to recover after you've been hit.
Share this post:
Related Posts
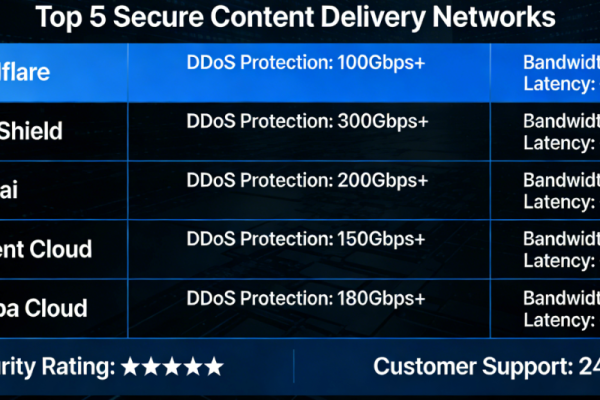
Hong Kong High-Defense CDN Recommendations (2026 Latest Edition)
Not all Hong Kong high-defense CDNs can withstand attacks. This article compares the protection stre...
No-ICP CDN Recommendations | Which Ones Actually Speed Up Mainland China AND Can Withstand Attacks?
How to choose a no-ICP CDN? Based on real webmaster tests, this article compares multiple CDN provid...
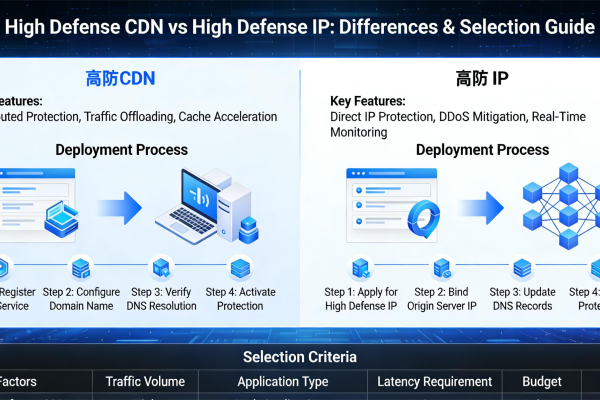
What's the Difference Between DDoS-Protected CDN and DDoS-Protected IP? A Clear Guide to Help You Choose.
What's the difference between a DDoS-protected CDN and a DDoS-protected IP? Which one should your we...
