Does High-Anti DDoS CDN Support WebSocket Protection? An Effective Security Solution for Real-Time Communication
The boss called at midnight saying the website was crippled by a DDoS attack. Staring at the plummeting traffic graph, I broke out in a cold sweat. Later, I realized high-anti DDoS CDNs actually CAN protect WebSocket—but there’s a lot of complexity here. Let’s talk about the pitfalls we’ve faced: how to tell real protection from fake, how deep protocol-layer protection needs to be, and how to conf

To be honest, the first time my boss woke me up at midnight to fix an emergency where the exchange’s WebSocket connections were crippled by a DDoS attack, I stared at the sharp, plummeting traffic line on the monitoring graph—my back was completely covered in cold sweat.
Real-time transaction data was all stuck, and users were flooding in with complaints. That feeling was truly awful.
Later, our team put in a lot of effort to research how high-anti DDoS CDNs protect WebSocket—and only then did we finally get a good night’s sleep.
To answer your question directly: Reliable high-anti DDoS CDNs definitely support WebSocket protection, and this is the cornerstone of securing real-time communication.
But there’s a lot more to it than that. You can’t just buy any CDN labeled “high-anti” and call it a day.
WebSocket (a persistent full-duplex channel established via the HTTP upgrade protocol) is inherently designed for real-time interaction. It’s the backbone of features like game battles, live customer support, financial market push notifications, and smart device control.
The downside? Its long-connection nature also makes it a prime target for hackers. Traditional HTTP Flood attacks have limited effect on it, but WebSocket-specific attacks—like protocol-layer CC attacks, Slowloris attacks, and resource exhaustion attacks—are extremely deadly.
We learned this the hard way: a CDN that claimed to support WebSocket protection completely collapsed as soon as it encountered a SYN flood mixed with malformed WebSocket protocol packet attacks.
So where was the problem? True WebSocket protection requires the CDN to perform in-depth parsing at the protocol layer.
Simply put, high-anti DDoS nodes can’t just act as “forwarders”—they need to work like experienced security inspectors: 
1. Sharp Eyes for the “Handshake” Phase:
The CDN must strictly verify the legitimacy of WebSocket Upgrade requests.
This includes checking the integrity of HTTP headers, Origin validation, the format of Sec-WebSocket-Key, and even blocking abnormal handshake requests based on frequency. Fake handshake packets? They get blocked right at the door.
2. A “Bomb Disposal Expert” for the Data Frame Layer:
WebSocket data transmission happens in frames. Malicious attacks often send malformed frames (such as oversized data frames or fragmented attack frames) to exhaust server resources.
A good high-anti DDoS CDN can parse frame structures in real time, filter illegal frames, and implement dynamic threshold controls for frame rate and packet size.
3. An “AI Detective” for Behavioral Patterns:
This is the key part. After a normal user establishes a WebSocket connection, their data interaction follows specific patterns (e.g., the frequency of chat messages, the interval between game operation commands).
Bot nodes controlled by hackers, however, often act abnormally—sending high-frequency empty data frames, or maintaining a large number of idle connections to hog resources.
The high-anti service we use (we won’t name it to avoid bias) has a self-developed AI engine that establishes a baseline for connection behavior. It marks and isolates “abnormal” connections in real time, which is far more accurate than just monitoring traffic volume.
4. A “Tough Nut” Against DDoS:
WebSocket attacks often combine large-scale Layer 3/4 DDoS attacks (such as UDP Flood, SYN Flood) for a “saturation attack,” trying to overwhelm the CDN node’s cleaning capacity.
This is where the CDN’s underlying bandwidth reserves and cleaning center capacity are put to the test.
I once witnessed this firsthand at a data center in Los Angeles: the cleaning center withstood a mixed attack of over 400 Gbps, while the traffic curve for the underlying WebSocket service barely fluctuated—that’s real capability.
Finally, a word of warning: Configuration optimization determines half the success. 
Remember to set up independent protection policies for WebSocket paths (e.g., /wss/) in the high-anti console—don’t mix them with regular HTTP traffic. Don’t set the connection timeout too long (30–120 seconds is recommended),
to avoid exploitation by slow attacks. Your origin server also needs to cooperate by adjusting TCP parameters (such as max connections, timewait recycling).
We once forgot to adjust the connection limit on our origin server. The high-anti CDN held off the attack, but our own Nginx was crushed by a flood of normal connections—it was pretty embarrassing.
At the end of the day, high-anti DDoS CDNs protecting WebSocket isn’t just a gimmick—it can truly be a lifesaver.
But don’t fall for marketing slogans. Focus on its ability to parse the protocol layer and the intelligence of its behavioral analysis.
Waking up at 3 a.m. to an attack alert is a feeling you’ll never want to experience again once you’ve been through it.
Choose the right solution, and your real-time communication services will truly stay rock-solid under the protection of a high-anti shield.
Share this post:
Related Posts
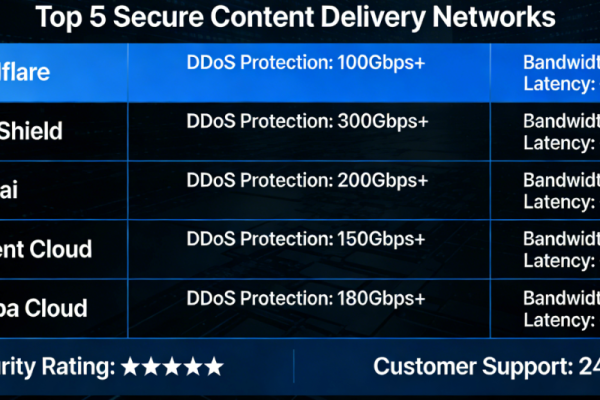
Hong Kong High-Defense CDN Recommendations (2026 Latest Edition)
Not all Hong Kong high-defense CDNs can withstand attacks. This article compares the protection stre...
No-ICP CDN Recommendations | Which Ones Actually Speed Up Mainland China AND Can Withstand Attacks?
How to choose a no-ICP CDN? Based on real webmaster tests, this article compares multiple CDN provid...
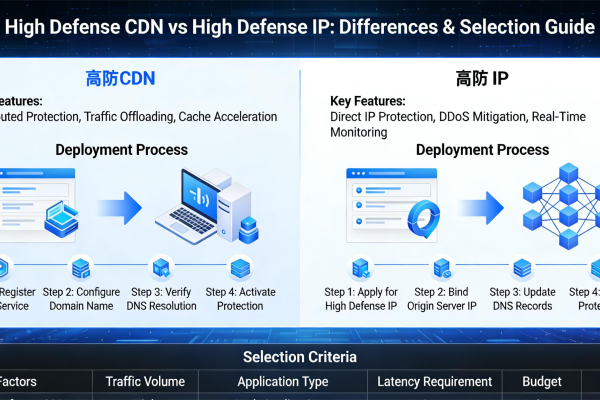
What's the Difference Between DDoS-Protected CDN and DDoS-Protected IP? A Clear Guide to Help You Choose.
What's the difference between a DDoS-protected CDN and a DDoS-protected IP? Which one should your we...
